 Cybersecurity Outsourcing
Cybersecurity OutsourcingCybersecurity Outsourcing Strategic Insights: Analysis 2025 and Forecasts 2033
Cybersecurity Outsourcing by Type (Network Security Assessment, Vulnerability Scanning, Data Encryption, Compliance Audit, Others), by Application (BFSI, IT & Telecom, Retail, Manufacturing, Healthcare, Others), by North America (United States, Canada, Mexico), by South America (Brazil, Argentina, Rest of South America), by Europe (United Kingdom, Germany, France, Italy, Spain, Russia, Benelux, Nordics, Rest of Europe), by Middle East & Africa (Turkey, Israel, GCC, North Africa, South Africa, Rest of Middle East & Africa), by Asia Pacific (China, India, Japan, South Korea, ASEAN, Oceania, Rest of Asia Pacific) Forecast 2025-2033
Key Insights
The global cybersecurity outsourcing market is projected to grow from $2496 million in 2025 to $5839 million by 2033, at a CAGR of 10.2% during the forecast period (2025-2033). The growth of the market is attributed to the increasing adoption of cloud-based security solutions, the rising number of cyber threats, and the growing need for organizations to comply with regulatory mandates.
The market is segmented by type into network security assessment, vulnerability scanning, data encryption, compliance audit, and others. The network security assessment segment is expected to hold the largest share of the market during the forecast period. The growth of this segment is attributed to the increasing demand for organizations to assess their network security posture and identify vulnerabilities. The vulnerability scanning segment is expected to grow at the highest CAGR during the forecast period. The growth of this segment is attributed to the increasing number of cyber threats and the need for organizations to identify and remediate vulnerabilities. The data encryption segment is expected to witness steady growth during the forecast period. The growth of this segment is attributed to the growing need for organizations to protect their sensitive data from unauthorized access. The compliance audit segment is expected to grow at a moderate CAGR during the forecast period. The growth of this segment is attributed to the increasing number of regulatory mandates that require organizations to audit their compliance with security standards.
The cybersecurity outsourcing market has witnessed significant growth in recent years, driven by the increasing demand for specialized cybersecurity services. This report provides a comprehensive analysis of the market, outlining key trends, driving forces, and challenges, along with insights into the leading players and significant developments.

Cybersecurity Outsourcing Trends
- Rising Cyber Threats: The frequency and sophistication of cyberattacks have prompted organizations to seek external expertise in mitigating risks and protecting sensitive data.
- Skill Shortage: The cybersecurity industry faces a shortage of qualified professionals, leading to increased outsourcing by organizations seeking access to skilled personnel.
- Cost Savings: Outsourcing cybersecurity functions can reduce operational expenses by eliminating the need for internal infrastructure, training, and recruitment costs.
- Improved Efficiency: External vendors specialize in cybersecurity and can provide more efficient and effective services than in-house teams, allowing organizations to focus on their core business.
- Compliance and Regulatory Requirements: Outsourcing can assist organizations in meeting regulatory compliance and standards, reducing the risk of penalties and liability.
Driving Forces: What's Propelling the Cybersecurity Outsourcing
- Exponential Increase in Data: The rapid growth of data volume necessitates robust cybersecurity measures, driving the demand for outsourced services.
- Evolving Cybersecurity Threats: The constantly evolving nature of cyber threats requires continuous monitoring and adaptation, making outsourcing a viable solution for organizations.
- Government Initiatives: Government agencies worldwide are emphasizing cybersecurity awareness and regulations, leading to increased demand for outsourcing services.
- Growing Adoption of Cloud-Based Services: Cloud computing adoption requires specialized cybersecurity measures,促进了外包市场的增长。
- Remote Workforce: The increasing adoption of remote work arrangements has expanded the attack surface and intensified the need for outsourced cybersecurity support.

Challenges and Restraints in Cybersecurity Outsourcing
- Data Security Concerns: Outsourcing cybersecurity services involves sharing sensitive data with external vendors, raising concerns about data security and privacy.
- Vendor Management Complexity: Organizations must carefully select and manage vendors to ensure service quality, reliability, and alignment with their cybersecurity objectives.
- Limited Control and Visibility: Outsourcing cybersecurity functions can reduce an organization's direct control over its security measures, potentially impacting response times and incident management.
- Cost Overruns: Unclear contracts and undisclosed pricing can lead to unexpected cost overruns, especially in long-term outsourcing arrangements.
- Reputational Risk: Cybersecurity breaches can damage an organization's reputation, and outsourcing can amplify this risk if vendors do not adhere to strict security protocols.
Key Region or Country & Segment to Dominate the Market
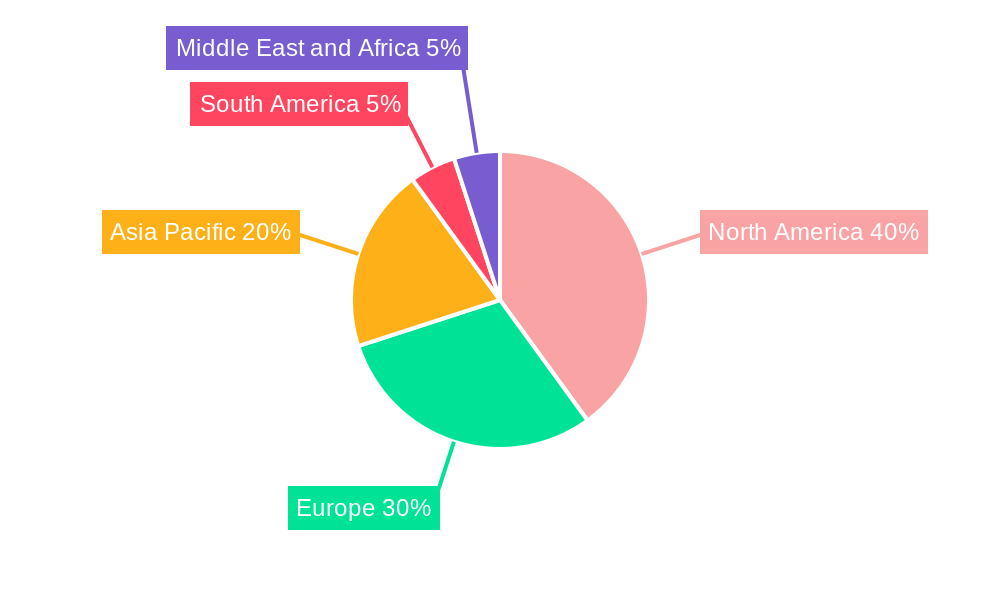
- Key Regions: North America and Europe are expected to dominate the cybersecurity outsourcing market due to high levels of IT adoption, regulatory compliance, and sophisticated cyberattacks.
- Key Segments:
- Application: BFSI, IT & Telecom, and Healthcare are projected to be the leading application segments, driven by their reliance on sensitive data and stringent regulatory requirements.
- Type: Network Security Assessment, Vulnerability Scanning, and Data Encryption are expected to witness significant growth as organizations seek proactive measures to detect and mitigate cyber threats.
Growth Catalysts in Cybersecurity Outsourcing Industry
- Advancements in AI and Machine Learning: The integration of AI and ML enables faster threat detection, automated incident response, and improved risk assessment.
- Cloud-Based Security Solutions: Cloud-based cybersecurity services offer scalability, flexibility, and cost-effectiveness, driving market growth.
- Increased Collaboration and Partnerships: Collaboration between cybersecurity vendors, technology providers, and organizations fosters innovation and enhances market offerings.
- Government Initiatives and Regulations: Government initiatives, such as cybersecurity frameworks and mandatory data protection laws, drive the adoption of outsourced cybersecurity services.
- Growing Awareness of Cybersecurity Risks: The increasing awareness of cybersecurity threats among organizations and individuals promotes the importance of outsourcing to protect valuable assets.
Leading Players in the Cybersecurity Outsourcing
- 7Security
- Aexus
- Aldridge
- Baker Tilly
- Cybalt
- Dirox Digital Solutions
- ITeXchange
- Nixu Cybersecurity
- Pharr Technologies
- Ricoh nofollow
- Savvycom
- Suntel Analytics
- ThreeIC
Significant Developments in Cybersecurity Outsourcing Sector
- Consolidation and Mergers: Strategic acquisitions and mergers are shaping the market landscape, creating larger players with a wider range of offerings.
- Innovation in Security Technologies: Emerging technologies, such as blockchain and quantum computing, are expected to revolutionize the cybersecurity industry and outsourcing landscape.
- Compliance-as-a-Service: Vendors are providing managed services that assist organizations in meeting regulatory compliance requirements, reducing the burden of internal compliance efforts.
- Cyber Insurance Integration: Cybersecurity outsourcing is increasingly combined with cyber insurance offerings, providing comprehensive protection for organizations against cyberattacks.
- Security Risk Management as a Service: Vendors offer comprehensive security risk management services that provide continuous monitoring, threat intelligence, and incident response support.
Comprehensive Coverage Cybersecurity Outsourcing Report
This comprehensive cybersecurity outsourcing report provides granular insights into the market dynamics, growth drivers, challenges, and key players. It offers invaluable data and analysis to assist organizations in evaluating their cybersecurity strategies and making informed outsourcing decisions.
Cybersecurity Outsourcing Segmentation
-
1. Type
- 1.1. Network Security Assessment
- 1.2. Vulnerability Scanning
- 1.3. Data Encryption
- 1.4. Compliance Audit
- 1.5. Others
-
2. Application
- 2.1. BFSI
- 2.2. IT & Telecom
- 2.3. Retail
- 2.4. Manufacturing
- 2.5. Healthcare
- 2.6. Others
Cybersecurity Outsourcing Segmentation By Geography
-
1. North America
- 1.1. United States
- 1.2. Canada
- 1.3. Mexico
-
2. South America
- 2.1. Brazil
- 2.2. Argentina
- 2.3. Rest of South America
-
3. Europe
- 3.1. United Kingdom
- 3.2. Germany
- 3.3. France
- 3.4. Italy
- 3.5. Spain
- 3.6. Russia
- 3.7. Benelux
- 3.8. Nordics
- 3.9. Rest of Europe
-
4. Middle East & Africa
- 4.1. Turkey
- 4.2. Israel
- 4.3. GCC
- 4.4. North Africa
- 4.5. South Africa
- 4.6. Rest of Middle East & Africa
-
5. Asia Pacific
- 5.1. China
- 5.2. India
- 5.3. Japan
- 5.4. South Korea
- 5.5. ASEAN
- 5.6. Oceania
- 5.7. Rest of Asia Pacific
Cybersecurity Outsourcing REPORT HIGHLIGHTS
| Aspects | Details |
|---|---|
| Study Period | 2019-2033 |
| Base Year | 2024 |
| Estimated Year | 2025 |
| Forecast Period | 2025-2033 |
| Historical Period | 2019-2024 |
| Growth Rate | CAGR of XX% from 2019-2033 |
| Segmentation |
|
Frequently Asked Questions
Is the market size provided in terms of value or volume?
The market size is provided in terms of value, measured in million .
Can you provide examples of recent developments in the market?
undefined
What is the projected Compound Annual Growth Rate (CAGR) of the Cybersecurity Outsourcing ?
The projected CAGR is approximately XX%.
How do I determine which pricing option suits my needs best?
The pricing options vary based on user requirements and access needs. Individual users may opt for single-user licenses, while businesses requiring broader access may choose multi-user or enterprise licenses for cost-effective access to the report.
What are the notable trends driving market growth?
.
Which companies are prominent players in the Cybersecurity Outsourcing?
Key companies in the market include 7Security,Aexus,Aldridge,Baker Tilly,Cybalt,Dirox Digital Solutions,ITeXchange,Nixu Cybersecurity,Pharr Technologies,Ricoh USA,Savvycom,Suntel Analytics,ThreeIC
What pricing options are available for accessing the report?
Pricing options include single-user, multi-user, and enterprise licenses priced at USD 4480.00 , USD 6720.00, and USD 8960.00 respectively.
What are the main segments of the Cybersecurity Outsourcing?
The market segments include
- 1. Introduction
- 1.1. Research Scope
- 1.2. Market Segmentation
- 1.3. Research Methodology
- 1.4. Definitions and Assumptions
- 2. Executive Summary
- 2.1. Introduction
- 3. Market Dynamics
- 3.1. Introduction
- 3.2. Market Drivers
- 3.3. Market Restrains
- 3.4. Market Trends
- 4. Market Factor Analysis
- 4.1. Porters Five Forces
- 4.2. Supply/Value Chain
- 4.3. PESTEL analysis
- 4.4. Market Entropy
- 4.5. Patent/Trademark Analysis
- 5. Global Cybersecurity Outsourcing Analysis, Insights and Forecast, 2019-2031
- 5.1. Market Analysis, Insights and Forecast - by Type
- 5.1.1. Network Security Assessment
- 5.1.2. Vulnerability Scanning
- 5.1.3. Data Encryption
- 5.1.4. Compliance Audit
- 5.1.5. Others
- 5.2. Market Analysis, Insights and Forecast - by Application
- 5.2.1. BFSI
- 5.2.2. IT & Telecom
- 5.2.3. Retail
- 5.2.4. Manufacturing
- 5.2.5. Healthcare
- 5.2.6. Others
- 5.3. Market Analysis, Insights and Forecast - by Region
- 5.3.1. North America
- 5.3.2. South America
- 5.3.3. Europe
- 5.3.4. Middle East & Africa
- 5.3.5. Asia Pacific
- 5.1. Market Analysis, Insights and Forecast - by Type
- 6. North America Cybersecurity Outsourcing Analysis, Insights and Forecast, 2019-2031
- 6.1. Market Analysis, Insights and Forecast - by Type
- 6.1.1. Network Security Assessment
- 6.1.2. Vulnerability Scanning
- 6.1.3. Data Encryption
- 6.1.4. Compliance Audit
- 6.1.5. Others
- 6.2. Market Analysis, Insights and Forecast - by Application
- 6.2.1. BFSI
- 6.2.2. IT & Telecom
- 6.2.3. Retail
- 6.2.4. Manufacturing
- 6.2.5. Healthcare
- 6.2.6. Others
- 6.1. Market Analysis, Insights and Forecast - by Type
- 7. South America Cybersecurity Outsourcing Analysis, Insights and Forecast, 2019-2031
- 7.1. Market Analysis, Insights and Forecast - by Type
- 7.1.1. Network Security Assessment
- 7.1.2. Vulnerability Scanning
- 7.1.3. Data Encryption
- 7.1.4. Compliance Audit
- 7.1.5. Others
- 7.2. Market Analysis, Insights and Forecast - by Application
- 7.2.1. BFSI
- 7.2.2. IT & Telecom
- 7.2.3. Retail
- 7.2.4. Manufacturing
- 7.2.5. Healthcare
- 7.2.6. Others
- 7.1. Market Analysis, Insights and Forecast - by Type
- 8. Europe Cybersecurity Outsourcing Analysis, Insights and Forecast, 2019-2031
- 8.1. Market Analysis, Insights and Forecast - by Type
- 8.1.1. Network Security Assessment
- 8.1.2. Vulnerability Scanning
- 8.1.3. Data Encryption
- 8.1.4. Compliance Audit
- 8.1.5. Others
- 8.2. Market Analysis, Insights and Forecast - by Application
- 8.2.1. BFSI
- 8.2.2. IT & Telecom
- 8.2.3. Retail
- 8.2.4. Manufacturing
- 8.2.5. Healthcare
- 8.2.6. Others
- 8.1. Market Analysis, Insights and Forecast - by Type
- 9. Middle East & Africa Cybersecurity Outsourcing Analysis, Insights and Forecast, 2019-2031
- 9.1. Market Analysis, Insights and Forecast - by Type
- 9.1.1. Network Security Assessment
- 9.1.2. Vulnerability Scanning
- 9.1.3. Data Encryption
- 9.1.4. Compliance Audit
- 9.1.5. Others
- 9.2. Market Analysis, Insights and Forecast - by Application
- 9.2.1. BFSI
- 9.2.2. IT & Telecom
- 9.2.3. Retail
- 9.2.4. Manufacturing
- 9.2.5. Healthcare
- 9.2.6. Others
- 9.1. Market Analysis, Insights and Forecast - by Type
- 10. Asia Pacific Cybersecurity Outsourcing Analysis, Insights and Forecast, 2019-2031
- 10.1. Market Analysis, Insights and Forecast - by Type
- 10.1.1. Network Security Assessment
- 10.1.2. Vulnerability Scanning
- 10.1.3. Data Encryption
- 10.1.4. Compliance Audit
- 10.1.5. Others
- 10.2. Market Analysis, Insights and Forecast - by Application
- 10.2.1. BFSI
- 10.2.2. IT & Telecom
- 10.2.3. Retail
- 10.2.4. Manufacturing
- 10.2.5. Healthcare
- 10.2.6. Others
- 10.1. Market Analysis, Insights and Forecast - by Type
- 11. Competitive Analysis
- 11.1. Global Market Share Analysis 2024
- 11.2. Company Profiles
- 11.2.1 7Security
- 11.2.1.1. Overview
- 11.2.1.2. Products
- 11.2.1.3. SWOT Analysis
- 11.2.1.4. Recent Developments
- 11.2.1.5. Financials (Based on Availability)
- 11.2.2 Aexus
- 11.2.2.1. Overview
- 11.2.2.2. Products
- 11.2.2.3. SWOT Analysis
- 11.2.2.4. Recent Developments
- 11.2.2.5. Financials (Based on Availability)
- 11.2.3 Aldridge
- 11.2.3.1. Overview
- 11.2.3.2. Products
- 11.2.3.3. SWOT Analysis
- 11.2.3.4. Recent Developments
- 11.2.3.5. Financials (Based on Availability)
- 11.2.4 Baker Tilly
- 11.2.4.1. Overview
- 11.2.4.2. Products
- 11.2.4.3. SWOT Analysis
- 11.2.4.4. Recent Developments
- 11.2.4.5. Financials (Based on Availability)
- 11.2.5 Cybalt
- 11.2.5.1. Overview
- 11.2.5.2. Products
- 11.2.5.3. SWOT Analysis
- 11.2.5.4. Recent Developments
- 11.2.5.5. Financials (Based on Availability)
- 11.2.6 Dirox Digital Solutions
- 11.2.6.1. Overview
- 11.2.6.2. Products
- 11.2.6.3. SWOT Analysis
- 11.2.6.4. Recent Developments
- 11.2.6.5. Financials (Based on Availability)
- 11.2.7 ITeXchange
- 11.2.7.1. Overview
- 11.2.7.2. Products
- 11.2.7.3. SWOT Analysis
- 11.2.7.4. Recent Developments
- 11.2.7.5. Financials (Based on Availability)
- 11.2.8 Nixu Cybersecurity
- 11.2.8.1. Overview
- 11.2.8.2. Products
- 11.2.8.3. SWOT Analysis
- 11.2.8.4. Recent Developments
- 11.2.8.5. Financials (Based on Availability)
- 11.2.9 Pharr Technologies
- 11.2.9.1. Overview
- 11.2.9.2. Products
- 11.2.9.3. SWOT Analysis
- 11.2.9.4. Recent Developments
- 11.2.9.5. Financials (Based on Availability)
- 11.2.10 Ricoh USA
- 11.2.10.1. Overview
- 11.2.10.2. Products
- 11.2.10.3. SWOT Analysis
- 11.2.10.4. Recent Developments
- 11.2.10.5. Financials (Based on Availability)
- 11.2.11 Savvycom
- 11.2.11.1. Overview
- 11.2.11.2. Products
- 11.2.11.3. SWOT Analysis
- 11.2.11.4. Recent Developments
- 11.2.11.5. Financials (Based on Availability)
- 11.2.12 Suntel Analytics
- 11.2.12.1. Overview
- 11.2.12.2. Products
- 11.2.12.3. SWOT Analysis
- 11.2.12.4. Recent Developments
- 11.2.12.5. Financials (Based on Availability)
- 11.2.13 ThreeIC
- 11.2.13.1. Overview
- 11.2.13.2. Products
- 11.2.13.3. SWOT Analysis
- 11.2.13.4. Recent Developments
- 11.2.13.5. Financials (Based on Availability)
- 11.2.1 7Security
- Figure 1: Global Cybersecurity Outsourcing Revenue Breakdown (million, %) by Region 2024 & 2032
- Figure 2: North America Cybersecurity Outsourcing Revenue (million), by Type 2024 & 2032
- Figure 3: North America Cybersecurity Outsourcing Revenue Share (%), by Type 2024 & 2032
- Figure 4: North America Cybersecurity Outsourcing Revenue (million), by Application 2024 & 2032
- Figure 5: North America Cybersecurity Outsourcing Revenue Share (%), by Application 2024 & 2032
- Figure 6: North America Cybersecurity Outsourcing Revenue (million), by Country 2024 & 2032
- Figure 7: North America Cybersecurity Outsourcing Revenue Share (%), by Country 2024 & 2032
- Figure 8: South America Cybersecurity Outsourcing Revenue (million), by Type 2024 & 2032
- Figure 9: South America Cybersecurity Outsourcing Revenue Share (%), by Type 2024 & 2032
- Figure 10: South America Cybersecurity Outsourcing Revenue (million), by Application 2024 & 2032
- Figure 11: South America Cybersecurity Outsourcing Revenue Share (%), by Application 2024 & 2032
- Figure 12: South America Cybersecurity Outsourcing Revenue (million), by Country 2024 & 2032
- Figure 13: South America Cybersecurity Outsourcing Revenue Share (%), by Country 2024 & 2032
- Figure 14: Europe Cybersecurity Outsourcing Revenue (million), by Type 2024 & 2032
- Figure 15: Europe Cybersecurity Outsourcing Revenue Share (%), by Type 2024 & 2032
- Figure 16: Europe Cybersecurity Outsourcing Revenue (million), by Application 2024 & 2032
- Figure 17: Europe Cybersecurity Outsourcing Revenue Share (%), by Application 2024 & 2032
- Figure 18: Europe Cybersecurity Outsourcing Revenue (million), by Country 2024 & 2032
- Figure 19: Europe Cybersecurity Outsourcing Revenue Share (%), by Country 2024 & 2032
- Figure 20: Middle East & Africa Cybersecurity Outsourcing Revenue (million), by Type 2024 & 2032
- Figure 21: Middle East & Africa Cybersecurity Outsourcing Revenue Share (%), by Type 2024 & 2032
- Figure 22: Middle East & Africa Cybersecurity Outsourcing Revenue (million), by Application 2024 & 2032
- Figure 23: Middle East & Africa Cybersecurity Outsourcing Revenue Share (%), by Application 2024 & 2032
- Figure 24: Middle East & Africa Cybersecurity Outsourcing Revenue (million), by Country 2024 & 2032
- Figure 25: Middle East & Africa Cybersecurity Outsourcing Revenue Share (%), by Country 2024 & 2032
- Figure 26: Asia Pacific Cybersecurity Outsourcing Revenue (million), by Type 2024 & 2032
- Figure 27: Asia Pacific Cybersecurity Outsourcing Revenue Share (%), by Type 2024 & 2032
- Figure 28: Asia Pacific Cybersecurity Outsourcing Revenue (million), by Application 2024 & 2032
- Figure 29: Asia Pacific Cybersecurity Outsourcing Revenue Share (%), by Application 2024 & 2032
- Figure 30: Asia Pacific Cybersecurity Outsourcing Revenue (million), by Country 2024 & 2032
- Figure 31: Asia Pacific Cybersecurity Outsourcing Revenue Share (%), by Country 2024 & 2032
- Table 1: Global Cybersecurity Outsourcing Revenue million Forecast, by Region 2019 & 2032
- Table 2: Global Cybersecurity Outsourcing Revenue million Forecast, by Type 2019 & 2032
- Table 3: Global Cybersecurity Outsourcing Revenue million Forecast, by Application 2019 & 2032
- Table 4: Global Cybersecurity Outsourcing Revenue million Forecast, by Region 2019 & 2032
- Table 5: Global Cybersecurity Outsourcing Revenue million Forecast, by Type 2019 & 2032
- Table 6: Global Cybersecurity Outsourcing Revenue million Forecast, by Application 2019 & 2032
- Table 7: Global Cybersecurity Outsourcing Revenue million Forecast, by Country 2019 & 2032
- Table 8: United States Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 9: Canada Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 10: Mexico Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 11: Global Cybersecurity Outsourcing Revenue million Forecast, by Type 2019 & 2032
- Table 12: Global Cybersecurity Outsourcing Revenue million Forecast, by Application 2019 & 2032
- Table 13: Global Cybersecurity Outsourcing Revenue million Forecast, by Country 2019 & 2032
- Table 14: Brazil Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 15: Argentina Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 16: Rest of South America Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 17: Global Cybersecurity Outsourcing Revenue million Forecast, by Type 2019 & 2032
- Table 18: Global Cybersecurity Outsourcing Revenue million Forecast, by Application 2019 & 2032
- Table 19: Global Cybersecurity Outsourcing Revenue million Forecast, by Country 2019 & 2032
- Table 20: United Kingdom Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 21: Germany Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 22: France Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 23: Italy Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 24: Spain Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 25: Russia Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 26: Benelux Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 27: Nordics Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 28: Rest of Europe Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 29: Global Cybersecurity Outsourcing Revenue million Forecast, by Type 2019 & 2032
- Table 30: Global Cybersecurity Outsourcing Revenue million Forecast, by Application 2019 & 2032
- Table 31: Global Cybersecurity Outsourcing Revenue million Forecast, by Country 2019 & 2032
- Table 32: Turkey Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 33: Israel Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 34: GCC Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 35: North Africa Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 36: South Africa Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 37: Rest of Middle East & Africa Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 38: Global Cybersecurity Outsourcing Revenue million Forecast, by Type 2019 & 2032
- Table 39: Global Cybersecurity Outsourcing Revenue million Forecast, by Application 2019 & 2032
- Table 40: Global Cybersecurity Outsourcing Revenue million Forecast, by Country 2019 & 2032
- Table 41: China Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 42: India Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 43: Japan Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 44: South Korea Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 45: ASEAN Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 46: Oceania Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
- Table 47: Rest of Asia Pacific Cybersecurity Outsourcing Revenue (million) Forecast, by Application 2019 & 2032
| Aspects | Details |
|---|---|
| Study Period | 2019-2033 |
| Base Year | 2024 |
| Estimated Year | 2025 |
| Forecast Period | 2025-2033 |
| Historical Period | 2019-2024 |
| Growth Rate | CAGR of XX% from 2019-2033 |
| Segmentation |
|
STEP 1 - Identification of Relevant Samples Size from Population Database



STEP 2 - Approaches for Defining Global Market Size (Value, Volume* & Price*)

Note* : In applicable scenarios
STEP 3 - Data Sources
Primary Research
- Web Analytics
- Survey Reports
- Research Institute
- Latest Research Reports
- Opinion Leaders
Secondary Research
- Annual Reports
- White Paper
- Latest Press Release
- Industry Association
- Paid Database
- Investor Presentations

STEP 4 - Data Triangulation
Involves using different sources of information in order to increase the validity of a study
These sources are likely to be stakeholders in a program - participants, other researchers, program staff, other community members, and so on.
Then we put all data in single framework & apply various statistical tools to find out the dynamic on the market.
During the analysis stage, feedback from the stakeholder groups would be compared to determine areas of agreement as well as areas of divergence
Related Reports
About Market Research Forecast
MR Forecast provides premium market intelligence on deep technologies that can cause a high level of disruption in the market within the next few years. When it comes to doing market viability analyses for technologies at very early phases of development, MR Forecast is second to none. What sets us apart is our set of market estimates based on secondary research data, which in turn gets validated through primary research by key companies in the target market and other stakeholders. It only covers technologies pertaining to Healthcare, IT, big data analysis, block chain technology, Artificial Intelligence (AI), Machine Learning (ML), Internet of Things (IoT), Energy & Power, Automobile, Agriculture, Electronics, Chemical & Materials, Machinery & Equipment's, Consumer Goods, and many others at MR Forecast. Market: The market section introduces the industry to readers, including an overview, business dynamics, competitive benchmarking, and firms' profiles. This enables readers to make decisions on market entry, expansion, and exit in certain nations, regions, or worldwide. Application: We give painstaking attention to the study of every product and technology, along with its use case and user categories, under our research solutions. From here on, the process delivers accurate market estimates and forecasts apart from the best and most meaningful insights.
Products generically come under this phrase and may imply any number of goods, components, materials, technology, or any combination thereof. Any business that wants to push an innovative agenda needs data on product definitions, pricing analysis, benchmarking and roadmaps on technology, demand analysis, and patents. Our research papers contain all that and much more in a depth that makes them incredibly actionable. Products broadly encompass a wide range of goods, components, materials, technologies, or any combination thereof. For businesses aiming to advance an innovative agenda, access to comprehensive data on product definitions, pricing analysis, benchmarking, technological roadmaps, demand analysis, and patents is essential. Our research papers provide in-depth insights into these areas and more, equipping organizations with actionable information that can drive strategic decision-making and enhance competitive positioning in the market.

